History of Secret Codes and Ciphers: The Evolution of Cryptology
Category: Cryptography
Unlocking the Past: Discover the History of Secret Codes and Ciphers
If you're a cryptography enthusiast, cybersecurity professional, or a student fascinated by the intertwined worlds of mathematics, history, and secret communications, you've landed in the right place. Understanding the history of secret codes and ciphers is crucial—not only to appreciate how far the field has evolved but also to grasp the foundations that modern encryption builds upon. Whether you’re seeking to deepen your knowledge of classical encryption methods or exploring how quantum technologies are beginning to reshape cryptology, this post offers a structured dive into centuries of coded secrets.
You likely arrived here wanting a comprehensive yet clear exploration that goes beyond just definitions, something that connects the dots between the cryptologic innovations of ancient civilizations and today’s quantum-safe algorithms. Perhaps you’ve faced the challenge of sifting through fragmented resources, lacking a coherent narrative that highlights key milestones, mathematical insights, and the broader implications of cipher evolution. This post is tailored specifically for you—it cuts through jargon to present an engaging, expert-level overview that links historical context with the mechanics and impact of secret communications through time.
Join us as we traverse from the rudimentary ciphers of antiquity to the sophisticated cryptanalysis of World Wars and ultimately, the dawn of quantum cryptography, showing how each era’s breakthroughs paved the way for secure digital communications in today’s interconnected world.
- Unlocking the Past: Discover the History of Secret Codes and Ciphers
- Origins of Secret Codes: Early Uses in Ancient Civilizations
- The Roman Legacy: Caesar Cipher and Political Secrecy
- Medieval and Renaissance Advancements: Polyalphabetic Ciphers and Cryptanalysis
- The Birth of Modern Cryptology: 19th Century Innovations and Machine Ciphers
- Cryptography in the World Wars: The Enigma, Navajo Code Talkers, and Beyond
- Transition to Digital Era: Public-Key Cryptography and Computational Foundations
- Contemporary Cryptographic Techniques: Symmetric, Asymmetric, and Hash Functions
- Quantum Impacts on Cryptography: Threats and Opportunities
- Secret Communications Beyond Ciphers: Steganography and Data Hiding Through History
- The Cultural and Societal Impact of Secret Codes: From Espionage to Privacy Movements
Origins of Secret Codes: Early Uses in Ancient Civilizations
The art of secret communication dates back millennia, with some of the earliest known cryptographic techniques emerging in ancient civilizations such as Egypt, Mesopotamia, and Classical Greece. These cultures recognized the strategic value of encoding messages to protect sensitive information—from military secrets to diplomatic correspondence—and laid the groundwork for systematic cryptography.
Egypt and Mesopotamia: The Dawn of Codified Secrecy
In Ancient Egypt, scribes occasionally employed rudimentary forms of substitution ciphers, replacing standard hieroglyphic signs with alternate or less common ones to obscure messages. Though not widespread, these early efforts reflect an understanding of obscurity as a security measure. Similarly, in Mesopotamia, scribes inscribed coded tablets using substitutions and non-standard language forms, primarily for administrative confidentiality or ritualistic purposes.
Classical Greece: The Birthplace of Systematic Ciphers
Classical Greece marks a crucial chapter in the evolution of secret codes, particularly with the documented use of the Scytale cipher by Spartan military leaders. This technique involved wrapping a strip of parchment around a rod (the scytale) to write a message; only a rod of the same diameter could decode it, exemplifying a transposition cipher methodology. Beyond this, simple substitution ciphers that replaced letters with alternate characters or symbols began appearing in Greek literature and military dispatches, showcasing a move towards more structured encryption methods.
These early civilizations highlight the fundamental principles of secret codes:
- Concealment through substitution and transposition
- Use of physical tools and symbolic transformations
- Strategic application in warfare, governance, and religion
Understanding these origins sets the stage for appreciating how mathematical rigor and computational techniques would later transform cryptology into the advanced science it is today.

Image courtesy of AXP Photography
The Roman Legacy: Caesar Cipher and Political Secrecy
Among the earliest and most influential ciphers in Western cryptographic history is the Caesar cipher, a simple yet effective substitution method famously attributed to Julius Caesar. This cipher involves shifting the letters of the alphabet by a fixed number of positions, typically three, to transform plaintext into an encoded message. Despite its apparent simplicity, the Caesar cipher played a pivotal role in securing military and political communications in the Roman Empire.
Julius Caesar’s strategic use of this cipher reflected a deep appreciation for secrecy in governance and warfare. By encoding orders, troop movements, and sensitive political correspondence, Caesar ensured that intercepted messages remained unintelligible to enemies and rival factions. The Caesar cipher’s ease of implementation allowed Roman officers to quickly encrypt and decrypt messages in the field without requiring specialized equipment or complex protocols, demonstrating the enduring value of practical cryptography in statecraft.
Key characteristics making the Caesar cipher revolutionary for its time include:
- Simplicity of substitution: Each letter is replaced by another letter shifted a fixed number of places.
- Uniformity of the algorithm: The same shift applies to the entire message, enabling straightforward encoding and decoding.
- Military and political functionality: It preserved secrecy while maintaining efficiency under battlefield or administrative constraints.
Although modern cryptanalysis easily breaks the Caesar cipher due to its limited key space, understanding this method reveals the roots of cryptographic thought in classical antiquity. It underscores how mathematical concepts such as modular arithmetic began to implicitly shape encryption practices, setting the stage for increasingly sophisticated ciphers in subsequent centuries. The Roman legacy thus embodies an early fusion of secrecy, strategic communication, and rudimentary mathematical principles that remain foundational to cryptology’s evolution.

Image courtesy of antonio filigno
Medieval and Renaissance Advancements: Polyalphabetic Ciphers and Cryptanalysis
The medieval and Renaissance periods mark a transformative chapter in the history of cryptography, characterized by the introduction of polyalphabetic ciphers and the emergence of systematic cryptanalysis. Moving beyond the limitations of simple monoalphabetic substitution ciphers like the Caesar cipher, scholars and cryptographers developed methods that significantly increased encryption complexity and security.
The Vigenère Cipher: A Pioneering Polyalphabetic System
One of the most influential advancements was the Vigenère cipher, invented in the 16th century and often hailed as the “unbreakable cipher” of its time. Unlike single-shift ciphers, the Vigenère used a keyword to apply multiple Caesar cipher shifts throughout the message, effectively creating a polyalphabetic system. This method disrupts the letter frequency patterns exploited in earlier cryptanalysis techniques, thus greatly enhancing message secrecy.
Key features of the Vigenère cipher include:
- Multiple cipher alphabets: Encryption cycles through a series of Caesar shifts defined by a repeating keyword.
- Resistance to frequency analysis: By varying letter substitution, the cipher masks predictable frequency distributions that made monoalphabetic ciphers vulnerable.
- Ease of use mixed with significant security gains: Offering both practical encryption and improved cryptographic strength.
The Birth of Cryptanalysis: Frequency Analysis and Early Breakthroughs
Parallel to these cipher innovations, the foundations of cryptanalysis—the science of breaking codes—were laid during this era. The 9th-century Arab mathematician and polymath Al-Kindi is credited with documenting the first known method of frequency analysis, a technique that analyzes the frequency of letters or groups of letters in ciphertext to infer the plaintext.
Frequency analysis exploits the fact that languages have characteristic letter distributions, providing a foothold for decrypting substitution ciphers. Although initially applied to monoalphabetic ciphers, early cryptanalysts experimented with ways to adapt this method to more complex systems.
Notable developments include:
- Recognition that letter frequency patterns can reveal substitution keys.
- Exploration of repetitions in ciphertexts, which would later influence techniques such as the Kasiski examination used to break polyalphabetic ciphers.
- The gradual emergence of cryptanalytic thought as a mathematical discipline, setting the foundation for modern codebreaking efforts.
Together, these medieval and Renaissance innovations bridged practical encryption with analytical decryption techniques, significantly advancing the field of cryptography. This period heralded a deeper understanding of the intricate relationship between cipher design and cryptanalysis, a dynamic that continues to drive cryptologic progress into the digital age and beyond.

Image courtesy of Mehdi Batal
The Birth of Modern Cryptology: 19th Century Innovations and Machine Ciphers
The 19th century stands as a pivotal era in cryptology, marking a revolutionary shift from manual ciphers to machine-assisted encryption and the proliferation of mathematical rigor in cipher design. This period laid the essential groundwork for the sophisticated cryptographic systems that would dominate the 20th century, dramatically expanding both the complexity and effectiveness of secret communications.
Mathematical Foundations and New Cipher Concepts
Advances in mathematics and logic deeply influenced cryptography during this time. The understanding of permutation theory and the formalization of combinatorics provided new insight into how symbols could be systematically rearranged and substituted. This mathematical sophistication enabled cryptographers to conceive ciphers with vastly larger key spaces than ever before, enhancing security against brute force and frequency analysis attacks.
Key developments include:
- Endorsement of polyalphabetic systems with improved key management, moving beyond fixed key sequences to more flexible and secure encryption models.
- The formulation of cryptographic principles based on algebraic structures, paving the way to conceptualize encryption as mathematical functions.
- Early recognition that automatic methods were essential to handle increasingly complex cipher transformations, which were too cumbersome for manual processing.
The Advent of Machine Ciphers: Mechanical Encryption Devices
One of the most transformative innovations of the 19th century was the creation of mechanical encryption devices designed to automate the ciphering process. These machines amplified encryption speed, accuracy, and complexity beyond manual capabilities, heralding the era of machine-assisted cryptology.
Among the earliest and most influential devices were:
- The Jefferson Disk (also known as Bazeries Cylinder): Invented by Thomas Jefferson in the late 18th century but becoming influential in the 19th, this device used a set of rotating disks with scrambled alphabets to perform polyalphabetic substitution. Message encoding involved aligning the disks in a secret order, dramatically increasing key complexity.
- The Wheatstone and Playfair ciphers: Although primarily manual, their mechanical adaptations enhanced operational efficiency and security based on digraphic substitution techniques.
- The evolution toward rotor machines: Models like the Enigma machine’s conceptual ancestors began to take shape, employing electrical rotors to enact polyalphabetic substitution on an unprecedented scale of complexity.
These innovations not only heightened encryption security but also introduced new challenges in cryptanalysis, stimulating the development of advanced codebreaking techniques. The symbiotic relationship between cipher machines and cryptanalysis would become a defining characteristic of modern cryptology.
By the end of the 19th century, the fusion of mathematics, engineering, and cryptography had set the stage for the explosive growth of secure communication technologies in the 20th century, fueling both civilian and military cryptographic advancements that would culminate in landmark breakthroughs during the World Wars and beyond.

Image courtesy of cottonbro studio
Cryptography in the World Wars: The Enigma, Navajo Code Talkers, and Beyond
The two World Wars marked a watershed moment in the history of cryptography, where secret codes and ciphers reached unprecedented levels of sophistication and strategic importance. Cipher machines, code talkers, and cryptanalysis efforts played pivotal roles in intelligence gathering and battlefield communications, directly influencing the outcomes of critical military campaigns and shaping modern cryptologic practices.
The Enigma Machine: A Breakthrough in Mechanical Cipher Technology
Perhaps the most iconic cryptographic device of the 20th century, the German Enigma machine, revolutionized wartime encryption by automating the process of polyalphabetic substitution through a complex system of rotating rotors and plugboard settings. This electromechanical device generated an astronomical number of possible configurations—estimated at over 10^114—making it appear unbreakable at the time.
Key aspects of the Enigma’s cryptographic strength included:
- Rotor-based scrambling: Each rotor shifted letters dynamically with every keystroke, creating a polyalphabetic cipher that evolved continuously.
- Plugboard (Steckerbrett): Allowed additional scrambling by swapping pairs of letters prior to rotor encryption, hugely expanding the key space.
- Daily key changes: Enigma operators altered rotor selections, starting positions, and plugboard wirings every day to reinforce security.
The Allied success in breaking Enigma codes, famously led by Alan Turing and his colleagues at Bletchley Park, exemplified the profound impact of cryptanalysis combined with emerging computing technologies. Decrypting Enigma-encrypted communications provided the Allies with critical intelligence (Ultra intelligence), enabling them to anticipate and counter Axis operations effectively.
Navajo Code Talkers: Unbreakable Human Ciphers in the Pacific Theater
In parallel to machine cryptography, the United States employed a uniquely human form of secure communication through the Navajo Code Talkers during World War II. These Native American Marines used the complex and unwritten Navajo language—unfamiliar to enemy forces—as a live, dynamic code to transmit tactical messages in the Pacific theater.
Highlights of the Navajo Code Talkers' contribution include:
- Development of a special code vocabulary correlating Navajo words to military terms, enhancing precision.
- Real-time voice encryption and decryption that bypassed electrical equipment, reducing vulnerability to interception.
- Proven unbreakability throughout the war, offering a secure communication channel that significantly expedited battlefield coordination and response.
Beyond Enigma and Code Talkers: The Broader Cryptographic Landscape
The World Wars also saw innovations such as:
- The SIGABA and Purple machines used by the United States, which advanced rotor machine designs and cipher complexity.
- One-time pad usage by agents and diplomatic corps, providing theoretically unbreakable encryption when keys were managed correctly.
- Rapid advancements in cryptanalysis techniques, including traffic analysis, statistical methods, and early computational assistance.
Collectively, these wartime cryptographic technologies and human-coded languages underscored how the integration of mechanical ingenuity, linguistic complexity, and mathematical principles shaped secure communication strategies. The successes and failures in this period remain foundational lessons for contemporary cryptologic systems, especially as modern encryption pivots toward quantum-resistant algorithms and next-generation cybersecurity paradigms.

Image courtesy of cottonbro studio
Transition to Digital Era: Public-Key Cryptography and Computational Foundations
The emergence of the digital age in the late 20th century revolutionized cryptography by introducing public-key cryptography, a groundbreaking paradigm shift that addressed the critical challenge of secure key exchange over insecure communication channels. Unlike classical symmetric ciphers, which require both sender and receiver to share a secret key in advance, public-key algorithms enable the use of separate keys for encryption and decryption, greatly enhancing scalability and security in digital communications.
The Dawn of Public-Key Cryptography: Diffie-Hellman and RSA
Public-key cryptography was first conceptualized in the seminal 1976 paper by Whitfield Diffie and Martin Hellman, who introduced the Diffie-Hellman key exchange protocol. This method relies on the mathematical hardness of the discrete logarithm problem in modular arithmetic to allow two parties to establish a shared secret key over an untrusted channel without prior coordination. The Diffie-Hellman algorithm laid the cryptographic foundation for secure communication in networked environments, igniting a wave of research into asymmetric encryption.
Shortly thereafter, in 1977, Ronald Rivest, Adi Shamir, and Leonard Adleman developed the RSA algorithm, which became the first widely adopted practical public-key encryption scheme. RSA’s security is based on the computational difficulty of factoring large composite numbers, particularly the product of two large prime numbers. This reliance on number theory gave rise to a new class of cryptographic systems grounded in rigorous mathematical principles and computational complexity assumptions.
Key mathematical foundations and features of RSA and Diffie-Hellman include:
- Modular exponentiation and arithmetic: Both algorithms operate over finite fields defined by large prime numbers.
- One-way functions: Functions that are easy to compute but hard to invert without secret information (e.g., factoring or discrete logarithm problems).
- Public and private key pairs: Separation of encryption and decryption keys enables secure distribution and authentication.
- Scalability: Suitable for digital environments where secure, automated key management is essential.
Computational Complexity: The Backbone of Modern Cryptography
Public-key cryptography introduced the crucial concept of computational hardness assumptions, which assert that certain mathematical problems are infeasible to solve efficiently with current computational resources. These assumptions underpin the security of modern encryption algorithms and drive ongoing research in cryptology. As computers grew more powerful, cryptographers sought to design algorithms that could withstand sophisticated attacks while remaining practical for everyday use.
The transition to digital cryptography brought about several advancements:
- Algorithmic encryption schemes leveraging number theory, algebraic structures, and complexity theory.
- Integration with digital signatures and cryptographic protocols to assure data integrity, authentication, and non-repudiation.
- Development of standardized cryptographic tools like PKI (Public Key Infrastructure), enabling widespread adoption of secure internet communications.
- The foundation for modern secure protocols, including SSL/TLS, which protect online banking, e-commerce, and confidential communications.
As digital technologies and the internet expanded globally, these public-key algorithms became the cornerstone of trustworthy digital security, enabling encrypted emails, secure websites, and confidential digital transactions. The evolution from manual and mechanical ciphers to algorithmically sophisticated, mathematically grounded systems highlights how theoretical advances and computational power reshaped cryptography for the information age.
This era sets the stage for ongoing cryptologic innovation, especially as the potential advent of quantum computing threatens existing cryptographic standards, prompting research into quantum-resistant algorithms and new cryptosystems that will secure the next generation of digital communication.

Image courtesy of Markus Winkler
Contemporary Cryptographic Techniques: Symmetric, Asymmetric, and Hash Functions
Modern cryptography underpins the security of virtually all digital communications, relying on a trio of foundational techniques to ensure confidentiality, integrity, and authentication. These contemporary cryptographic methods—symmetric encryption, asymmetric encryption, and cryptographic hash functions—each play distinct but complementary roles in safeguarding data across networks, financial systems, and personal devices.
Symmetric Encryption: Speed and Efficiency in Secret Sharing
Symmetric encryption employs a single shared secret key for both encrypting and decrypting messages. Algorithms such as AES (Advanced Encryption Standard) and ChaCha20 dominate this space due to their efficiency and robust security properties. Symmetric ciphers are especially well-suited for encrypting large volumes of data quickly, making them ideal for securing database records, VPN tunnels, and encrypted file storage.
Key attributes of symmetric encryption include:
- Shared secret key requirement: Both sender and receiver must securely exchange and protect the same key.
- High performance: Low computational overhead enables fast encryption and decryption, optimizing real-time communication.
- Use cases: Bulk data encryption, securing communication channels (e.g., TLS), encrypted backups, and disk encryption.
However, symmetric methods face critical challenges around key distribution and management, particularly in large networks or open environments—issues which asymmetric cryptography helps address.
Asymmetric Encryption: Secure Key Exchange and Digital Signatures
In contrast, asymmetric encryption utilizes a pair of mathematically linked keys: a public key for encryption and a private key for decryption. This key pair framework, exemplified by algorithms like RSA, Elliptic Curve Cryptography (ECC), and ElGamal, solves the key exchange problem inherent in symmetric systems by enabling secure communication without prior secret sharing.
Important features of asymmetric cryptography are:
- Public-private key pairs: The public key can be freely distributed, while the private key remains confidential.
- Support for digital signatures: Authenticating message origin and integrity through cryptographic signing and verification.
- Key exchange protocols: Secure generation of symmetric session keys used in hybrid encryption schemes.
Typical applications include encrypted email (PGP/GPG), SSL/TLS handshake protocols securing web browsers, and blockchain transaction authentication. While asymmetric encryption is computationally more intensive than symmetric, hybrid systems combining both methods optimize security and performance.
Cryptographic Hash Functions: Ensuring Data Integrity and Authentication
Cryptographic hash functions like SHA-256 and SHA-3 provide fixed-length, unique message digests from arbitrary input data. These functions are one-way and collision-resistant, ensuring that even a tiny change in input drastically alters the output hash. Hashes form the backbone of data integrity verification, password storage, and digital signatures.
Core properties and use cases include:
- Deterministic output: The same input always yields the same hash.
- Pre-image resistance: Infeasible to reconstruct original input from the hash.
- Collision resistance: Extremely low probability of two distinct inputs producing the same hash.
- Applications: File integrity checks, message authentication codes (MACs), blockchain proof-of-work, and password hashing with salt.
Together, symmetric encryption, asymmetric encryption, and hash functions create multi-layered cryptographic systems that underpin the secure digital ecosystem. These techniques not only protect data confidentiality and integrity but also authenticate identities in an increasingly interconnected world—providing a resilient defense in the face of emerging threats, including those posed by advancing computational capabilities and prospective quantum attacks.

Image courtesy of Markus Winkler
Quantum Impacts on Cryptography: Threats and Opportunities
The advent of quantum computing introduces both profound threats and promising opportunities for the field of cryptography. Quantum computers leverage principles of quantum mechanics—such as superposition and entanglement—to perform computations that classical computers cannot efficiently handle. This paradigm shift challenges the security assumptions underlying many widely used cryptosystems today, especially those based on factoring large numbers and discrete logarithms.
Quantum Threats to Classical Cryptography
Quantum algorithms, most notably Shor’s algorithm, enable polynomial-time factorization of large integers and computation of discrete logarithms. This capability directly undermines the security of foundational cryptosystems, including:
- RSA (Rivest–Shamir–Adleman): Relies on the difficulty of factoring large primes—a challenge quantum computers can solve efficiently.
- Elliptic Curve Cryptography (ECC): Secured by the hardness of elliptic curve discrete logarithm problems, also vulnerable to Shor’s algorithm.
- Diffie–Hellman Key Exchange: Based on discrete logarithms; subject to quantum attacks.
Consequently, the integrity of digital communications, e-commerce transactions, and data confidentiality risks compromise as quantum hardware continues to progress toward practical scalability. Moreover, Grover’s algorithm offers a quadratic speedup for brute-force key searches against symmetric encryption, necessitating longer key lengths to maintain security.
Development of Quantum-Resistant Algorithms
To counteract quantum threats, the cryptographic community is actively developing and standardizing post-quantum cryptography (PQC)—algorithms designed to be secure against both classical and quantum attacks. Candidates leverage mathematical problems currently believed to resist quantum algorithms, including:
- Lattice-based cryptography: Utilizing hard problems in algebraic lattices, such as Learning With Errors (LWE) and Ring-LWE.
- Code-based cryptography: Based on decoding problems for linear error-correcting codes, exemplified by McEliece cryptosystems.
- Multivariate polynomial cryptography: Involving the difficulty of solving systems of nonlinear polynomial equations over finite fields.
- Hash-based signatures: Providing secure digital signatures relying solely on hash function properties.
Institutions like the National Institute of Standards and Technology (NIST) are spearheading standardization efforts by evaluating these post-quantum algorithms through rigorous security and performance assessments. Transitioning global cryptographic infrastructure to quantum-resistant standards is essential to future-proof digital security against emerging quantum capabilities.
Opportunities in Quantum Cryptography
Beyond resisting quantum attacks, quantum cryptography itself offers novel secure communication mechanisms, the most prominent being Quantum Key Distribution (QKD). QKD exploits the fundamental laws of quantum physics to enable two parties to generate a shared secret key with guaranteed security. Any eavesdropping attempt disturbs the quantum state, revealing the presence of an interceptor and allowing immediate countermeasures.
Key advantages of quantum cryptography include:
- Information-theoretic security: Security guaranteed by physics rather than computational hardness assumptions.
- Real-time eavesdropping detection: Intrinsic to the quantum measurement process.
- Integration potential: Increasingly combined with classical cryptographic protocols for hybrid secure systems.
Preparing for the Quantum Future
The transition toward a quantum-safe cryptographic ecosystem mandates proactive adaptation in cryptographic design, implementation, and policy. Critical steps include:
- Auditing existing cryptosystems for vulnerabilities to quantum attacks.
- Investing in post-quantum research and development to deploy practical, scalable quantum-resistant algorithms.
- Encouraging hybrid cryptographic models combining classical and post-quantum methods during the transition period.
- Raising awareness and training cybersecurity professionals on quantum threats and defenses.
As quantum computing evolves from theory to practical reality, its influence on cryptography represents both a monumental threat to legacy encryption and a catalyst for unprecedented innovation. Embracing quantum-resistant algorithms and quantum communication technologies today is vital to safeguarding the privacy and security of tomorrow’s digital world.
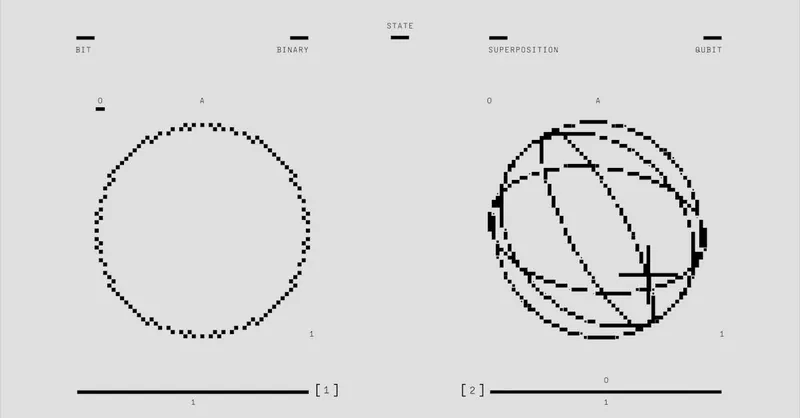
Image courtesy of Google DeepMind
Secret Communications Beyond Ciphers: Steganography and Data Hiding Through History
While ciphers and codes have been the cornerstone of secret communications, history reveals a parallel tradition of concealing information using methods beyond direct encryption. Among these, steganography—the art of hiding messages within innocuous-looking media—and other data hiding techniques have played critical roles in covert communication strategies, complementing cipher systems by adding an additional layer of secrecy.
Early Steganographic Practices
Steganography dates back thousands of years, with some of the earliest recorded instances emerging in ancient civilizations, including:
- Invisible Inks and Hidden Writing: Ancient Greeks reportedly used substances like lemon juice or milk to write invisible messages on parchment, which only became visible when heated. Similarly, ancient Indians and Chinese scribes developed plant-based or chemical inks that concealed messages in seemingly blank documents.
- Tattooing Messages: Herodotus recounts how the Greek historian Histiaeus sent secret orders by shaving a slave’s head, tattooing the message on his scalp, and waiting for the hair to grow back before sending him to the recipient.
- Microdot Techniques: Though a more modern development, the precursor concept appeared in earlier eras where tiny, compressed messages were hidden within larger texts or artworks, allowing covert transmission without attracting suspicion.
Complementing Encryption with Concealment
Steganographic techniques have been used historically not to replace ciphers but to supplement them, often creating multi-layered security methods by combining:
- Encrypted messages concealed within a medium—for example, a ciphertext hidden in a painting, letter, or piece of music.
- Physical concealment, such as hiding written messages inside hollow objects or embedding data in seemingly mundane artifacts.
- Code words or phrases embedded in natural language texts, where the true message is extracted by a predetermined method known only to communicating parties.
This dual approach of data hiding plus encryption enhances operational security during message transmission, making interception and detection by adversaries significantly more difficult.
Evolution Toward Digital Steganography and Data Hiding
The principles of ancient steganography have seamlessly transitioned into the digital era, evolving into sophisticated digital steganography techniques, such as:
- Embedding confidential information within multimedia files—images, audio, or video—by manipulating less perceptible elements like color values or sound frequencies.
- Utilizing watermarking and covert channels for protecting intellectual property and enabling hidden communication within network protocols.
- Deploying advanced statistical and algorithmic methods to ensure that data embedding is imperceptible and resistant to tampering or detection.
By understanding the historical interplay between traditional ciphers and complementary secret communication techniques like steganography, we gain a richer perspective on the multi-dimensional nature of secrecy across ages. This knowledge underscores the importance of combining mathematical encryption foundations with practical concealment strategies—a duality that continues to shape contemporary methods of secure communication, especially in an age where digital data permeates every aspect of life.

Image courtesy of Daniel Nava
The Cultural and Societal Impact of Secret Codes: From Espionage to Privacy Movements
Secret codes and ciphers have long transcended their technical origins to profoundly influence societal trust, political power dynamics, and the global discourse on privacy and surveillance. From their pivotal role in espionage during wartime to shaping the modern privacy movement in the digital age, cryptography has consistently affected how individuals and nations negotiate secrecy, transparency, and control.
Espionage and the Shaping of Global Power
Historically, the use of secret codes has been integral to intelligence gathering and military strategy, serving as both a weapon and a shield in conflicts. Espionage operations, such as those employing Enigma decrypts in World War II or Cold War cryptanalytic endeavors, illustrate how codes can alter geopolitical trajectories by enabling covert information access or denying it to adversaries. The shadowy domain of intelligence reveals cryptography’s double-edged nature—while it protects state secrets, it also fuels espionage arms races and ethical dilemmas over surveillance.
Trust, Transparency, and the Social Contract
At the societal level, secret codes influence public trust and governance. Governments use encryption to safeguard sensitive communications but also engage in debates over lawful access and censorship, raising questions about how much secrecy is justified in democratic societies. The tension between state security and individual privacy rights exemplifies how cryptographic tools intersect with citizen freedoms, impacting everything from whistleblowing to journalism, activism, and public accountability.
Privacy Movements and the Rise of Digital Encryption
In the contemporary digital era, secret codes underpin the privacy movement that advocates for secure communications against unauthorized surveillance by states, corporations, and malicious actors. The popularization of end-to-end encryption in messaging platforms like Signal and WhatsApp reflects a widespread demand for confidentiality, data protection, and digital self-determination. These developments demonstrate how cryptography shifts from an exclusive military or governmental tool to a civilian necessity, empowering individuals to control their digital footprints and communicate without fear of interception.
Ongoing Debates: Balancing Security, Privacy, and Accessibility
The societal impact of secret codes continues to evolve amidst contentious debates involving:
- Backdoors and government mandates: Should encryption systems include built-in access points for law enforcement, or do such measures irrevocably weaken security?
- Mass surveillance vs. privacy rights: How can societies balance collective security needs with safeguarding civil liberties in an age of pervasive data collection?
- Cryptography’s role in combating misinformation: How do secure communications affect the spread of truthful information and the fight against disinformation?
By investigating these facets, we recognize that secret codes are not merely technical artifacts but powerful social instruments shaping trust, control, and freedom in a complex world. Understanding this cultural and societal impact is crucial for anyone interested in the broader implications of cryptography beyond mathematical constructs and algorithms—highlighting its vital role in navigating the challenges of privacy, security, and human rights in the modern digital landscape.
Image courtesy of Lucas Andrade
